| Regarding backslash character Before you start, if the USER or PWD part of the string to be hashed contains a '\' character, start instead at section 1.2 Generate and change credentials (with '\' character) below. |
This page references Automated Agent Registration and is designed to quickly get you started monitoring hosts with GDMA. Outlined below are the steps necessary to configure an existing GroundWork server to support GDMA agents, and install and configure the agent on Linux and Windows hosts. Solaris installations are similar to Linux, with the exception of the location of the agent directories and certain paths.
| As of the Windows GDMA 2.6.1 release, it is possible for a site to run the GDMA service as a non-administrative user, see Windows GDMA as non-admin user before you install the agent. |
CONTENTS | RELATED RESOURCES | WAS THIS PAGE HELPFUL? |
The credentials used by the deployed GDMA agents needs to be added to the JBoss Application Server so calls to the legacy REST API succeed. By default the server is configured to use the credentials gdma/gdma, however it is recommended to change the password regularly. Follow the steps below on the GroundWork Monitor server to add the credentials to the authentication store.
| Regarding backslash character Before you start, if the USER or PWD part of the string to be hashed contains a '\' character, start instead at section 1.2 Generate and change credentials (with '\' character) below. |
In the properties file the GDMA default password is set to gdma=8ae0d35b1f513c066178c3eaf805a0fa. To change the password you need to first create a MD5 Hex. In the example below we use: {USER}: gdma, {PWD}: #changeME and the command: echo -n "{USER}:ApplicationRealm:{PWD}"|md5sum
echo -n gdma:ApplicationRealm:#changeME|md5sum
Which produces a MD5 Hex value:
6f46676d7c793eaae2ed13f5bb676a46
vi /usr/local/groundwork/jpp/standalone/configuration/application-users.properties
gdma=8ae0d35b1f513c066178c3eaf805a0fa
gdma=6f46676d7c793eaae2ed13f5bb676a46
echo -n autoreg:ApplicationRealm:NewPassword|md5sum 1e2dc18f4f9094d342fdb60feb907f47
autoreg=1e2dc18f4f9094d342fdb60feb907f47
| Ensure there are no additional characters, including spaces, following the MD5 hex value when editing this file, as this will cause auto-registration to fail. |
| Dual JBoss Systems Before you continue, if you are running a dual JBoss system you will need to change an additional file as described below. To check if you are running a dual JBoss system enter the command: ps -ef | grep java Dual JBoss systems will have two processes starting with: "/usr/local/groundwork/java/bin/java -D[Standalone]"
|
In the case of the USER or PWD part of the string to be hashed contains a '\' character, the '\' characters must be properly escaped before piping to md5sum. For example one might use the netbios naming convention domain\username with a password such as A\gjhjhg. Both '*' characters in this case must be properly escaped before piping to md5sum. Use the string \u005c in every place that you have a '*'.
In the properties file the GDMA default user and password is set to gdma=8ae0d35b1f513c066178c3eaf805a0fa. To change the password you need to first create a MD5 Hex. In the example below we use: {DOMAIN}/{USER}: example.com/gdma, {PWD}: A\gjhjhg, and the command: echo -n "{DOMAIN}{USER}:ApplicationRealm:{PWD}"|md5sum
echo -n example.com\u005cgdma:ApplicationRealm:A\u005cgjhjhg|md5sum
Which produces a MD5 Hex values:
29aecce20dfaf39c0050696d5d9b9589
vi /usr/local/groundwork/jpp/standalone/configuration/application-users.properties
gdma=8ae0d35b1f513c066178c3eaf805a0fa
example.com\gdma=29aecce20dfaf39c0050696d5d9b9589
| Dual JBoss Systems Before you continue, if you are running a dual JBoss system you will need to change an additional file as described below. To check if you are running a dual JBoss system enter the command: ps -ef | grep java
|
The first section below outlines steps to configure a GroundWork Monitor server as the target server for GDMA results and a source for GDMA configuration data. The next section outlines the configuration for GDMA client servers.
| The following steps should be followed for new installations and upgrades. If you are upgrading an existing GDMA target server the following steps may already be in place however should be verified. |
vi /usr/local/groundwork/config/bronx.cfg
# LISTENER MAX PACKET IMMINENCE # The max allowed "future age", in seconds, of the passive check result received. # Any newer results are dropped to the floor. # The maximum allowed value is "900" seconds. # Set the value to "0" to disallow passive checks with newer timestamps. # If not specified, the value will be "1" second, which should be just # enough to allow for possible slight discrepancies which can arise even # between time-synchronized client and server machines. In general, we # highly recommend that the site use NTP or similar time-synchronization # software to tie together the software clocks on disparate machines to # high accuracy, to prevent misunderstandings about when events actually # occur. Note that time synchronization for a VM guest machine can be # problematic; see your vendor's documentation on this topic. # The GroundWork-recommended value is 900, largely because Windows # machines often have trouble maintaining Internet time synchronization. listener_max_packet_imminence=900 \\ \\ # USE CLIENT TIMESTAMP # This parameter, if set to a positive value, configures the listener thread # to use the timestamp in the passive check result received for processing, # rather than the time on the server when the check result is processed. # To prevent confusion in handling data from clients which are not # time-synchronized to the server, such a check result timestamp will be # automatically overridden and replaced with the server timestamp if the # passive check result timestamp is found by the server to be in the future. # If not specified, the value will be "1". #use_client_timestamp=0
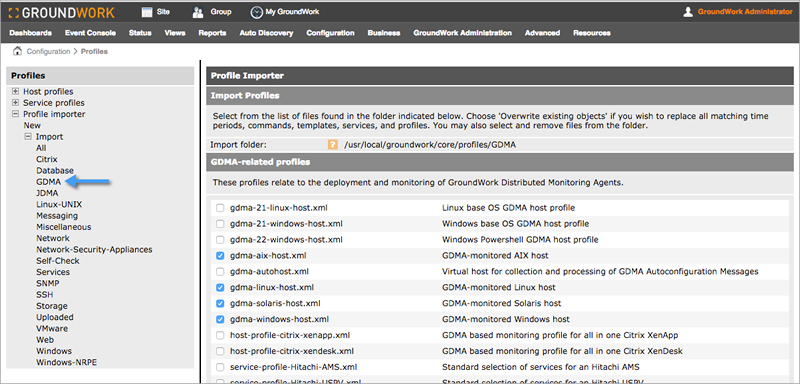
| If upgrading an existing GDMA client server, start with step 1. Uninstall the legacy client. If this is a new installation, start with step 2. Download the agent. |
/usr/local/groundwork/uninstall
rm -Rf /usr/local/groundwork
vi /usr/local/groundwork/apache2/conf/httpd.conf
<Directory /usr/local/groundwork/apache2/htdocs/agents>
Options +Indexes -FollowSymLinks -ExecCGI -Includes
AllowOverride None
Order Allow,Deny
Allow from all
</Directory>
/etc/init.d/groundwork restart apache
chmod +x groundworkagent-2.6.1-103-linux-64-installer.run
./groundworkagent-2.6.1-103-linux-64-installer.run
GDMA requires clock synchronization between this system and the master GroundWork system. Before installing, ensure that the clock on this system is correct. GDMA requires network name resolution (DNS) to locate and communicate with the master GroundWork system. Before installing, ensure that name resolution is functional on this system. Continue? [Y/n]: Y
Make sure to enter the name of the GroundWork server in place of [gdma-autohost].
Enter the name of the GroundWork server. This can be a resolvable short name, a fully-qualified domain name, or an IP address. It will be used to download the configuration for this agent, as well as to send the monitoring results to. Target Server [gdma-autohost]:
Please select which protocol will be used for communication with the GroundWork server. [1] HTTP [2] HTTPS: If you choose HTTPS, you will need to manually set up certificates as well. Please choose an option [1] :
Use the credentials here you added in section 1.0 above.
Enter the user name and password to be used for auto-registration of this GDMA machine. If these credentials are not provided, auto-registration will be disabled on this machine, and the older auto-configuration protocol will be used instead. Registration username []: Registration password:
Enter the host profile and service profile names to be applied to this machine's monitoring setup during auto-registration. These values are optional; if left blank, the host profile will be defaulted on the server, and no extra service profile will be applied. Host profile name [gdma-linux-host]: Service profile name []:
Do you want to start the GDMA service after the installation? [Y/n]:
Setup is now ready to begin installing GroundWork Distributed Monitoring Agent on your computer. Do you want to continue? [Y/n]:
| As of the Windows GDMA 2.6.1 release (supported in GroundWork Monitor 7.2.0 and bundled into GroundWork Monitor 7.2.1 and later), it is possible for a site to run the GDMA service as a non-administrative user. Many customers would prefer this, as a means of limiting the overall security profile of this service. Before installation please refer to the document Windows GDMA as non-admin user. |
GDMA requires clock synchronization between this system and the master GroundWork system. Before installing, ensure that the clock on this system is correct. GDMA requires network name resolution (DNS) to locate and communicate with the master GroundWork system. Before installing, ensure that name resolution is functional on this system. Continue? Yes
Welcome to the GroundWork Distributed Monitoring agent Setup Wizard.
Installation directory: c:\Program Files (x86)\groundwork.
Enter the name of the GroundWork server. This can be a resolvable short name, a fully-qualified domain name, or an IP address. It will be used to download the configuration for this agent, as well as to send the monitoring results to. Target Server:
It is important to read the article, Windows GDMA as non-admin user, regarding the username entry on this screen. By passing the username and password entries will default to running GDMA as an administrator. This is the correct setup in nearly all cases. Only if you were installing as an ordinary user, which should be rare, would you need to provide a password.
Please specify the user name to be used by the Agent. GDMA username: GDMA user password needed? (only for an ordinary user account) GDMA user password
Please select which protocol will be used for communication with the GroundWork server. HTTP or HTTPS: If you choose HTTPS, you will need to manually set up certificates as well. Next.
Enter the user name and password to be used for auto-registration of this GDMA machine. If these credentials are not provided, auto-registration will be disabled on this machine, and the older auto-configuration protocol will be used instead. Registration username: e.g., gdma Registration password: e.g., gdma Re-enter password: e.g., gdma. Next.
Enter the host profile and service profile names to be applied to this machine's monitoring setup during auto-registration. These values are optional; if left blank, the host profile will be defaulted on the server, and no extra service profile will be applied. Host profile name: e.g., gdma-windows-host, Service profile name: <blank>. Next.
Setup is now ready to begin installing GroundWork Distributed Monitoring Agent on your computer. Next.